So went the very first words of a recent catch-up conversation with the Head of Information Security at a major government department who knows that the thing I normally initially ask her is what (work-related issue) is keeping her awake at night at the moment. When asked to elaborate she said she felt that they managed risk well internally but that it was the supply chain, especially third and even fourth parties that worried her. She had concerns about both the detail of the contracts with her third parties but, more importantly, she didn’t really know what data might be exposed in the event of a breach somewhere in her supply chain.
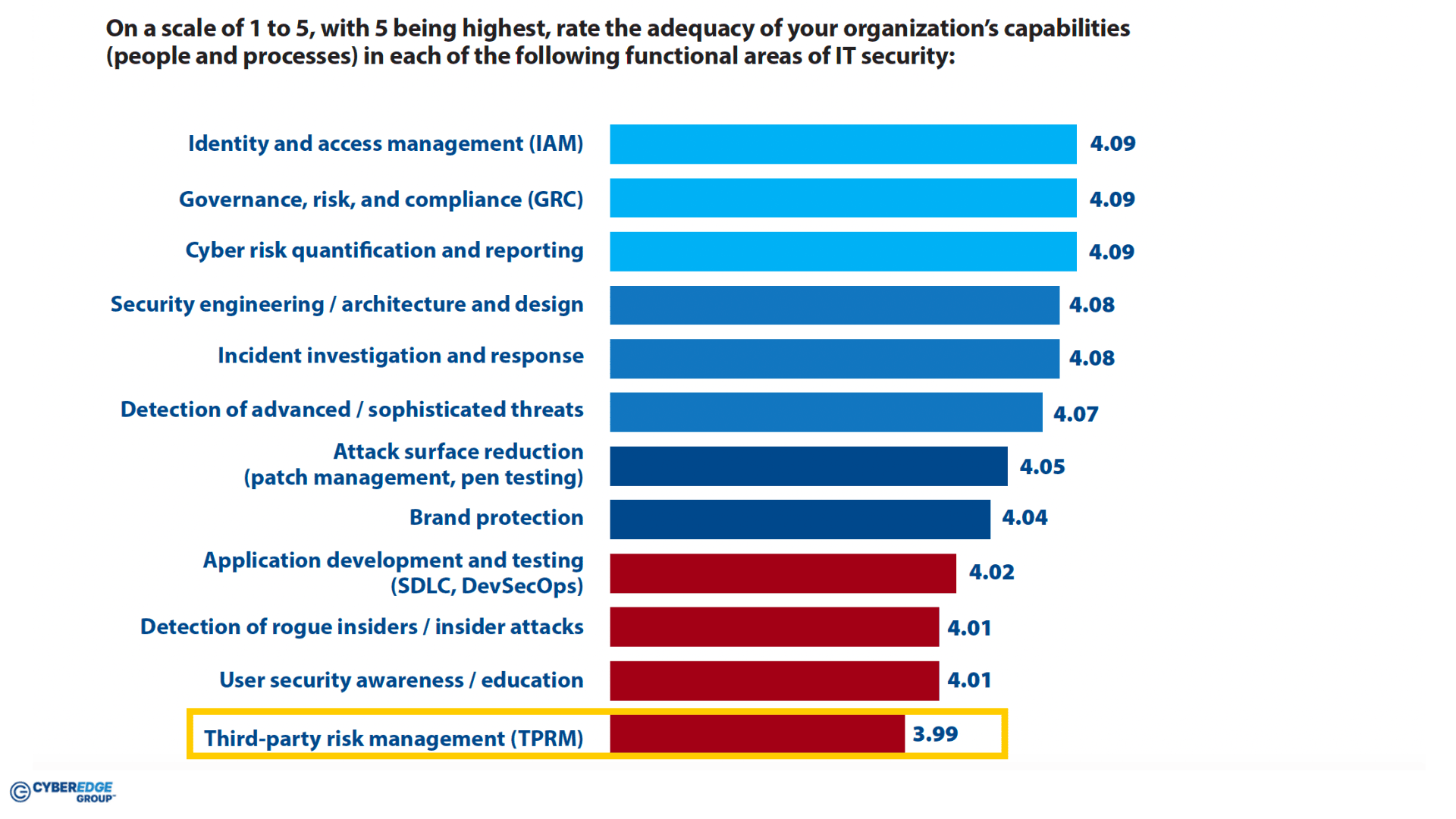
And she is not alone. Each year, since 2014, CyberEdge1 has carried out a cross industry, international survey of IT security professionals to assess their security posture, perceptions of cyberthreats and IT security challenges, current and future security investments, and IT security practices and strategies. The recently released 2024 report captured data from 1,200 respondents in 17 countries across 19 industries. One of their key questions concerns the respondent’s view of the adequacy of their organisation’s capability in a list of functional areas. As you would expect, those functional areas in the red zone of low capability include application development and testing, detection of rogue insiders and user security and awareness. However, sitting squarely at the bottom of the list is third-party risk management (TPRM).
In terms of impact, supply chain issues can be enormous. In 2022, The world’s largest carmaker Toyota shut down all of its plants across Japan after a suspected cyber-attack on one of the carmaker’s largest parts suppliers resulted in a loss of production of 13,000 cars per day.
So, it is clear that TPRM is a big issue everywhere and can potentially have existential consequences. As such, it is something that the data protection and information security practices at Oyster IMS have been dealing with for a number of years. Our team of qualified and experienced consultants can help you to map and then manage all the processes associated with your supply chain enabling you to understand your dependence on third parties and potential points of risk. We can also support you with ongoing management of supplier contracts and help you to understand associated risk. We are also aware that managing third parties is more than just a onetime assessment. It is a relationship that must be managed throughout the TPRM lifecycle and includes all your processes and technologies around third-party supplier selection, onboarding, assessment, risk mitigation, monitoring, and eventually offboarding.
Working with Oyster IMS in the areas of third-party and supplier risk management can help you:
- Gain insight into the information security considerations that could be easily enforced via contracts
- Be better prepared to respond to supply chain related cyber incidents
- Have confidence in your suppliers’ security practices and build long term partnerships through a repeatable assessment methodology
- Reduce the likelihood of a cyber-attack or breach through on-going monitoring and regular re-assessment.
And it just might be one less thing to keep you awake at night.
1: Source: 2024 Cyberthreat Defense Report, CyberEdge Group, LLC.

